Register SAP BTP, Cloud Foundry Subaccount in Identity Authentication Service
Beginner
25 min.
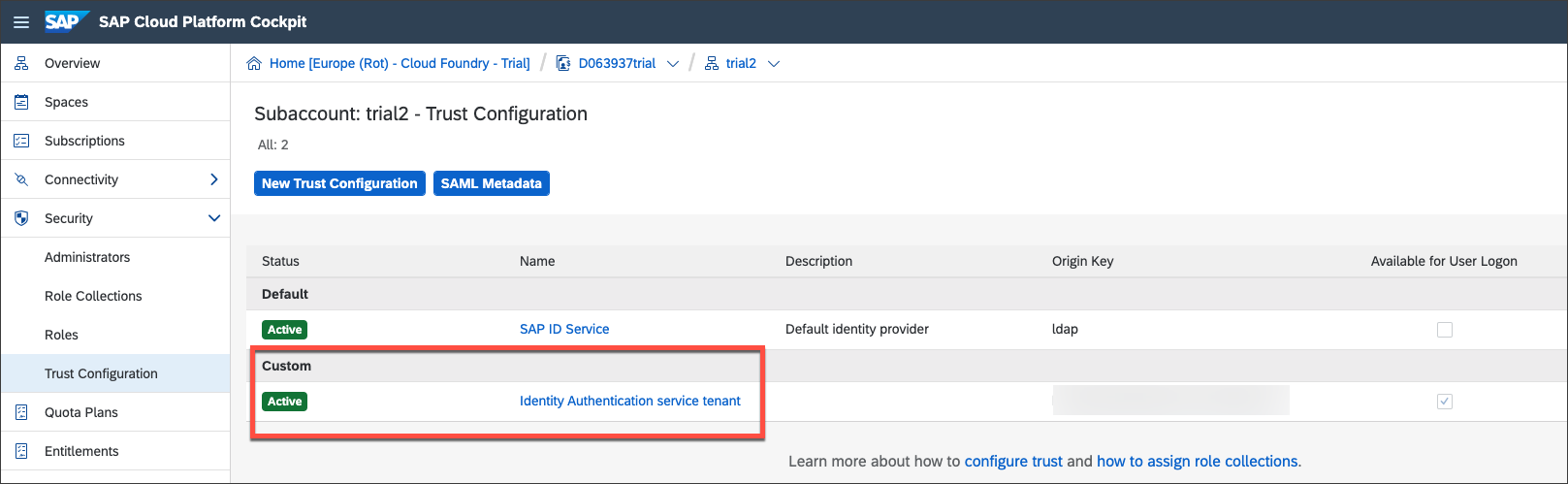
Establish trust between a SAML 2.0 identity provider in SAP Cloud Identity Services - Identity Authentication and an SAP BTP, Cloud Foundry subaccount.
You will learn
- How to establish trust between your SAP BTP, Cloud Foundry subaccount and the Identity Authentication service
- How to configure users for single sign-on usage
Prerequisites
- You have a Free Trial Account on SAP Business Technology Platform. See Get a Free Account on SAP BTP Trial.
- You have a tenant of Identity Authentication service. See Tenant Model and Licensing.
- You have an Azure Active Directory (Azure AD) account. See Sign Up for Microsoft Azure
Congratulations!
You have successfully connected Azure Active Directory with your Identity Authentication tenant. Furthermore, the SAP BTP, Cloud Foundry subaccount can now: leverage all the capabilities of Identity Authentication service, for instance users can login with their mail address of Azure Active Directory (as long as their account is part of the Azure Active Directory and the enterprise application).
Good Job!